
August 18, 2020
Good morning, everyone!
| This week’s critical vulnerabilties: Patch Tuesday was BIG this month! The Register says We spent way too long on this Microsoft, Intel, Adobe, SAP, Red Hat Patch Tuesday article. Just click on it, pretend to read it, apply updates and frankly that’s pretty good advice. Also, critical security patch released for Amazon’s Alexa, and Citrix released critical updates for its XenMobile Endpoint Management server. |
Complacency is the Death Knell of Cybersecurity
The Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency (CISA) says “Resources and talent only go so far if you're not aware of which systems are most vulnerable and still clicking on phishing emails.” Senior intelligence officials at CISA, NCSC and the FBI at a workshop last week said that we "need to get back to basics” and ”practice vigilance and consistency.” As Professor Moody says, "Constant Vigilance!"
Back to Basics
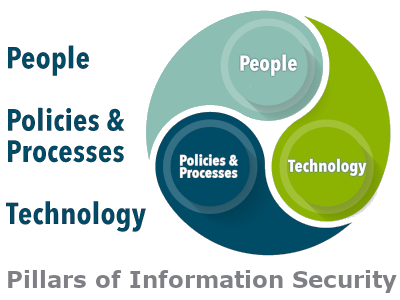
Remember, the Pillars of Information Security are People, Policies and Processes, and Technology. You cannot throw enough technology at this problem to make it go away! If that were possible, large corporations wouldn’t have data breaches. But they do. In fact, sometimes technology actually makes things worse:
The use of too many different cybersecurity tools is weakening companies’ cyber-resilience, according to the latest research published by the Ponemon Institute.
I’m sure your mama told you “too much of a good thing is not a good thing” didn’t she? That’s true even in the case of anvirus/antimalware software on your PC. Loading two or three applications doesn’t make you more secure; in fact, it can open holes in your defenses as the products interfere with one another. Choose one comprehensive, well-rated application and uninstall the others. With the plethora of devices and operating systems we have these days, there is no one product that is best in all situations. PC Magazine does pretty good reviews from time to time. Worth reading.
So where do we start? The answer is going Back to Basics.
You can’t secure it if you don’t know it’s there
The 20 CIS Controls have long been considered the canonical standard for network security. Let’s look at the first two:
- Inventory and Control of Hardware Assets
- Inventory and Control of Software Assets
So we start by conducting an inventory and documenting it. Without this basic information, it is difficult (if not impossible) to secure information systems. In addition to asset inventory lists, good documentation includes:
- Network diagrams
- Device configuration information
- Maintenance/support agreements
- Account/access lists
- Organizational chart with roles & responsibilities identified
- Network security & acceptable use policies
- Incident response plan
- Disaster recovery plan
- Business continuity plan
With good documentation, you know what you have, you know how it's configured, you know who has access to it, you know why you need it, and you know how to replace it in an emergency.
Why is this important? Well, let’s ask NASA: Last year, NASA’s Jet Propulsion Laboratory was hacked because of an unauthorized device on its network, placed there by an employee ”without authorization or going through the proper security review” (this is known as "Shadow IT" and it’s a growing problem).
But it’s not just government agencies or even big companies! I can’t tell you how often we discover critical issues on a security audit for a small business when we find devices or software on the network, installed by an employee with no understanding of the dangers. Often it’s a wireless access device without proper configuration. Sometimes it’s software that uploads company information to third-party servers on the Internet.
How do you protect your company against Shadow IT?
- Have a written security policy It should include things like a prohibition on providing hardware and software without proper authorization. (See my white paper ”Protecting Company Data with Simple Security Policies” for more on this subject.)
- Train your employees Not just on the policy specifics, but why the policy is in place. Use examples like the NASA JPL hack. Tell stories, make the policy come alive to your employees. People remember stories!
- Use technology Regular internal and external scans can provide the data you need to identify unapproved hardware and software on your network.
As always, I could talk a lot more about this! Come back next week for the next installment.
Security Awareness Training Goes Virtual
Thanks to COVID-19, lots of things are going virtual, and that includes my employee Security Awareness Training. I've set up
a small studio in our conference room (nobody there but me) so I can provide live training (almost) just like before!
You can see me wave my hands and make faces while a wall of fascinating facts and practical tips slideshow across your screens, wherever
you and your employees may be.
Contact me to schedule your employee training sessions. They're fun! ☺
Remember, you can read past editions of this newsletter on our website, along with tons more information under the Resources tab of our new website.
Talk to you again soon!

Glenda R. Snodgrass
grs@theneteffect.com
(251) 433-0196 x107
https://www.theneteffect.com
For information security news & tips, follow me!
